MASSIVE 20GB LEAK FROM INTEL DOCUMENTS BACKDOORS IN ALL INTEL CPUS
SOURCE: BLEEPING COMPUTER
Classified and confidential documents from U.S. chipmaker Intel, allegedly resulting from a breach, have been uploaded earlier today to a public file sharing service.
The cache of secret information is 20GB large and comes from an unknown source. It was announced as the first part in a series of Intel leaks.
According to Tillie Kottmann, a developer and reverse engineer who received the documents from an anonymous hacker, most of the information is supposed to be protected intellectual property. The developer was told that the information was stolen from Intel in a breach this year.
"They were given to me by an Anonymous Source who breached them earlier this year, more details about this will be published soon," Kottmann says.
“Most of the things here have NOT been published ANYWHERE before and are classified as confidential, under NDA or Intel Restricted Secret,” the developer added.
Those browsing firmware source code will find comments referring to backdoors, but that could mean anything and does not necessarily mean they can gain access to your computer:
An Intel spokesperson replying to our request for comments pointed us to the company’s product security policy page, which states that "Intel product development policy and practices prohibit any intentional steps to allow undocumented device access (e.g., “backdoors”), exposure of sensitive device information, or a bypass of security features or restrictions of its products."
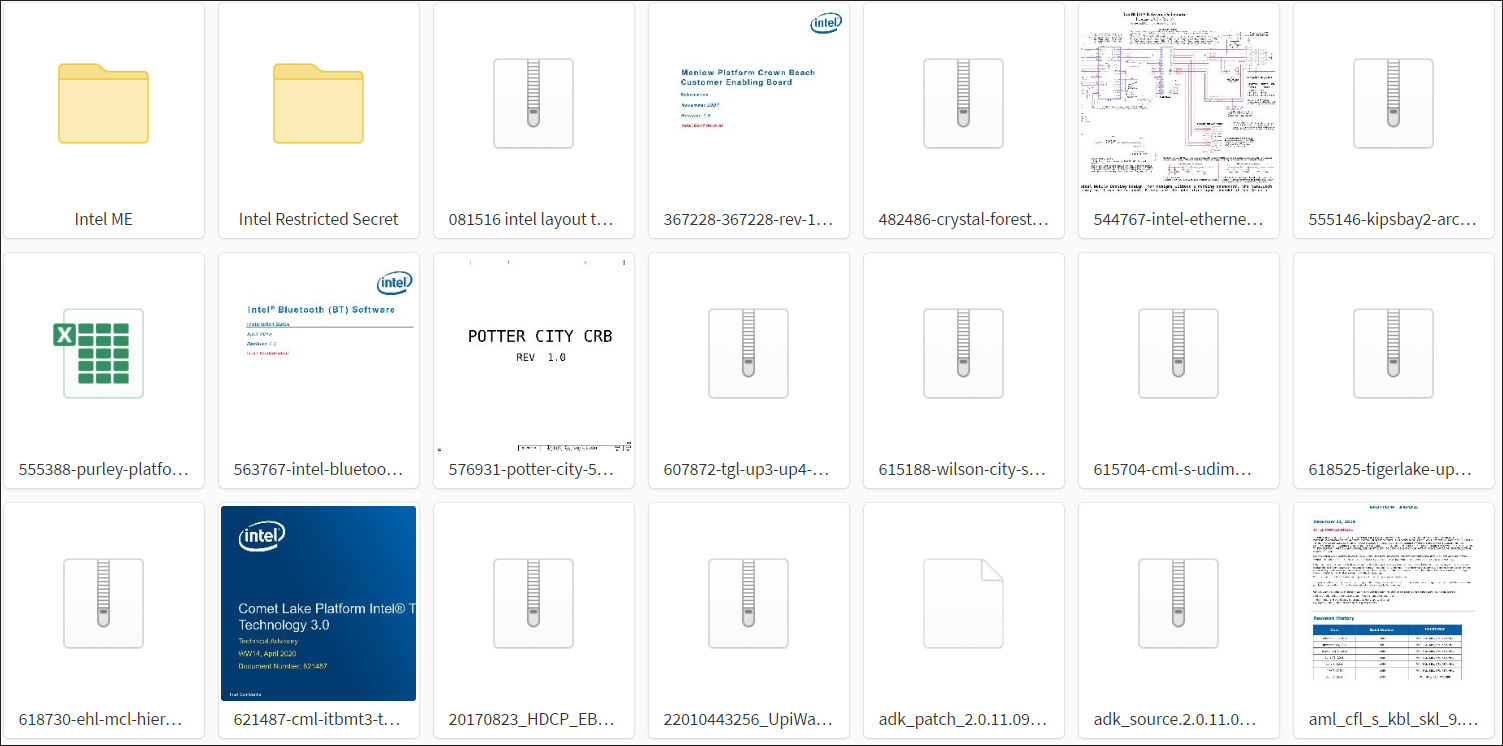
Some of the files in the archive include technical specifications and relate to internal chipset design, including Kaby Lake platform and Intel Management Engine (ME).
This initial release contains documents related to the following:
- Intel ME Bringup guides + (flash) tooling + samples for various platforms
- Kabylake (Purley Platform) BIOS Reference Code and Sample Code + Initialization code (some of it as exported git repos with full history)
- Intel CEFDK (Consumer Electronics Firmware Development Kit (Bootloader stuff)) SOURCES
- Silicon / FSP source code packages for various platforms
- Various Intel Development and Debugging Tools
- Simics Simulation for Rocket Lake S and potentially other platforms
- Various roadmaps and other documents
- Binaries for Camera drivers Intel made for SpaceX
- Schematics, Docs, Tools + Firmware for the unreleased Tiger Lake platform
- (very horrible) Kabylake FDK training videos
- Intel Trace Hub + decoder files for various Intel ME versions
- Elkhart Lake Silicon Reference and Platform Sample Code
- Some Verilog stuff for various Xeon Platforms, unsure what it is exactly
- Debug BIOS/TXE builds for various Platforms
- Bootguard SDK (encrypted zip)
- Intel Snowridge / Snowfish Process Simulator ADK
- Various schematics
- Intel Marketing Material Templates (InDesign)
This release has already been dubbed “juicy” but Kottmann believes that future leaks from their source are likely to contain even “juicier” classified documents.
HOW IT ALLEGEDLY HAPPENED
Kottman is maintaining a repository with source code obtained by them and various sources hunting for misconfigured devops tools that allow access to resources. The repository contains data, proprietary code included, from dozens of companies (GE Appliances, Microsoft, Qualcomm, Motorola, AMD, Lenovo).
The developer does their best to remove sensitive information from the code they publish and complies with takedown requests. Even more, they are willing to provide details about the misconfiguration and how to avoid mishaps in the future.
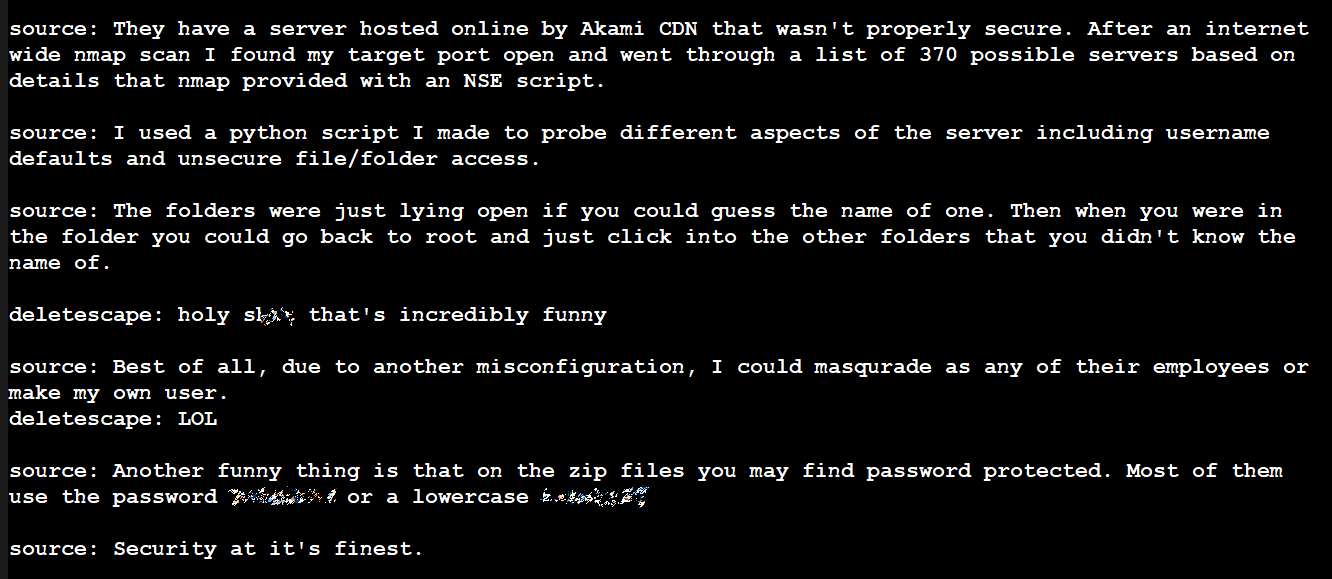
The Intel breach appears to be no different. The hacker told Kottmann that they found an Intel server on a CDN that was not properly secured. This particular machine was seemingly selected based on details collected from an internet-wide scan.
Using a custom Python script, the hacker claims they were able to test for default username access and unsecured access to files and folders. According to the hacker, access to the folders was possible if you knew the right names. They needed to guess just one name, though. Once in, they could go back to the root directory and get access to any of them.
The chat above originally contained passwords for Intel documents that BleepingComputer intentionally removed.
However, the more important detail provided was the claim that they could impersonate any Intel employee with access to the resources, or create their own user. Some of the files are archives protected by an incredibly weak password.
In a statement to BleepingComputer, Intel said that the data appears to be from the Intel Resource and Design Center. A company representative did not speculate on the breach method but said that the leak may be from someone with access to the portal:
“We are investigating this situation. The information appears to come from the Intel Resource and Design Center, which hosts information for use by our customers, partners and other external parties who have registered for access. We believe an individual with access downloaded and shared this data” - Intel representative
Employees in this department have higher than normal privileges that give them access not just to resources for customers and OEMs but also to Intel’s intellectual property like documentation and tools, testing services, and pre-release product info, all available under a corporate non-disclosure agreement (CNDA).
This is a developing story...
SHARE THIS ARTICLE...
Israel IS Intel
"Destroying the New World Order"
THANK YOU FOR SUPPORTING THE SITE!
Latest Activity
- Top News
- ·
- Everything
Ghislaine Maxwell & The Secret "Shadow" 9/11 Commission? | John Kiriakou
When the Communists Take Over America!...Famous 1957 Anti-Communist Movie
When the Communists Take Over America!...Famous 1957 Anti-Communist Movie
Are the End Times Drawing Near?
Catherine Fitts: Epstein, CIA Black Budget, the Control Grid, and the Banks’ Role in War
Ключові слова в тексті: як органічно їх вписати в статтю
© 2026 Created by truth.
Powered by
![]()
You need to be a member of 12160 Social Network to add comments!
Join 12160 Social Network