Election 2020 Was Rigged: The Evidence
Election 2020 Was Rigged: The Evidence
Decisive (but not widespread) election fraud occurred on November 3:
- Smartmatic election software was developed in Venezuela with porous security and built-in functionality allowing system administrators to override the security features it appeared to incorporate. Among the extraordinary privileges it granted to administrators were abilities to:
- shave votes continuously from one candidate to another;
- batch ballots for later “adjudication” but which instead became a pool of votes that the administrator could simply assign to the candidate of choice;
- generate blank ballots.
- Through a string of opaque licensing agreements, bankruptcies, and corporate mergers and acquisitions, that software ended up in election systems (e.g., Dominion) for use in the USA and other countries. The fact that elections systems developed under Hugo Chavez were managing elections in the USA began to strike some Americans as unfortunate.
- In a New York Times 2006 article (“U.S. Investigates Voting Machines’ Venezuela Ties”), journalist Brad Golden wrote, “The federal government is investigating the takeover last year of a leading American manufacturer of electronic voting systems by a small software company that has been linked to the leftist Venezuelan government of President Hugo Chávez. The inquiry is focusing on the Venezuelan owners of the software company, the Smartmatic Corporation, and is trying to determine whether the government in Caracas has any control or influence over the firm’s operations…”
- In 2008, VoterAction (an activist group based in Massachusetts and Washington State) issued a public report (“SEQUOIA VOTING SYSTEMS, INC. USES VOTE-COUNTING SOFTWARE DEVELOPED, OWNED, AND LICENSED BY FOREIGN-OWNED SMARTMATIC, A COMPANY LINKED TO THE VENEZUELAN GOVERNMENT OF HUGO CHÁVEZ”) where they noted: “U.S. national security is potentially at risk because software used to count votes in 20% of the country during U.S. elections is owned and controlled by a Venezuelan-run company with ties to the Venezuelan government of Hugo Chávez,1 which has been described as ‘the foremost meddler in foreign elections in the Western hemisphere.’2 Foreign-owned and foreign-run Smartmatic’s control over vote counting software used in the voting machines of Sequoia Voting Systems… presents a potential national security risk now just as it did in 2006 when the U.S. Committee on Foreign Investment in the United States (“CFIUS”) opened an investigation of Smartmatic’s ownership of Sequoia.3 CFIUS is a U.S. government inter-agency committee led by the U.S. Department of Treasury that addresses national security risks posed by foreign ownership of or influence over U.S. business, including companies providing the means by which voters in the U.S. elect their President and Congressional Representatives.4 Rather than answer to CFIUS regarding the ultimate owners of the Smartmatic conglomerate5 and its ties to the Chávez government, an investment group led by Sequoia management reportedly bought Sequoia from Smartmatic in late 2007 under terms that were not made public.6 Since then, however, it has come to light that Smartmatic continues to own the software that counts the votes on Sequoia voting machines and licenses to Sequoia that software, which Smartmatic develops in Venezuela.7 Concern, now, is that Smartmatic’s sale of Sequoia “was fraudulent”,8 “a sham transaction designed to fool regulators.”9 Efforts to date have not succeeded in determining the ultimate owners of Smartmatic or the extent to which Smartmatic and the Chávez government of Venezuela have influence over U.S. elections through Smartmatic’s control of the software that counts votes for Sequoia voting machines…”
- See this recent Phillipines TV interview where Smartmatic’s chairman Mark Malloch-Brown (who, oddly enough, also serves as Vice-Chairman of George Soros’s investment fund and ...) initially danced around such Venezuelan connections (note his oh-so-careful parsing of words in this regard) before eventually acknowledging the licensing arrangement between D....
- The Smartmatic (a.k.a. Sequoia) running on various brands of US election systems (of which Dominion is only one) brought to US elections not only overly-generous functionality, but porous security permitting manipulation not just by administrators, but by those outside the precinct and even abroad.[1] These functionalities were strategically & aggressively used to rig the US election on November 3.
- It was strategic in that it was not “widespread” but targeted at six cities[2] which, if flipped, also would flip the swing states in which they are found (and thus, the electoral college);
- It was aggressive for the simple reason that Trump broke their algorithm, because he was on his way to a win that exceeded their ability to overcome through minor cheats alone. It is for that reason that in those six locations the bad guys went full-on-goon (e.g., thugs intimidating observers, newspapers taped over windows, “water main breaks” shutting down counting then immediately reopened once Republican observers had departed, etc.)
- Proof of this is found in three forms that dovetail perfectly;
- Documentation of the extraordinary administrator privileges embedded within Dominion’s systems;
- Affidavits from voters and volunteers describe experiences that match exactly what they would experience in locations being gooned by the measures to which I refer;[3]
- Data (such as that displayed extensively below) expressing outrageous statistical oddities (e.g., thousands and tens of thousands of sequential Biden votes that occur with quadrillion-to-1 improbability, ballot processing spikes at velocities that were physically impossible given available site equipment) that themselves coincide with windows of intense and aggressive intimidation of and interference with those observing the voting and counting.
- In each of several swing states Biden achieved a come-from-behind victory with a margin in the tens-of-thousands of votes thanks to getting hundreds of thousands of votes through these measures.
Conclusion: The US 2020 election was wildly compromised: it is an egg that can’t be unscrambled.
[1] Dominion’s servers are widely infected with QSnatch malware. As poll-workers (e.g., administrators) log-in, QSnatch steals their credentials. Thus not only can administrators override (with no audit trail) election security in a precinct, so can anyone who steals those credentials (which, given the ubiquity of QSnatch on Dominion servers, happens everywhere). Dominion sends out software patches that continuously (deliberately?) allow QSnatch to beat their patches.
[2] Atlanta, Philadelphia, Detroit, Milwaukee, Maricopa County Arizona (Greater Phoenix), Clark County Nevada (Greater Las Vegas).
[3] By way of example: Sharpie/Bic switcheroos experienced in Maricopa precincts reflect a wish to generate a large pool of “adjudicated ballots” for administrators, who could drag-and-drop them later to Candidate Biden.
*Pardon bad formatting. Have been tweaking it but I delayed long enough getting this live. I have continued expanding this though November 24.
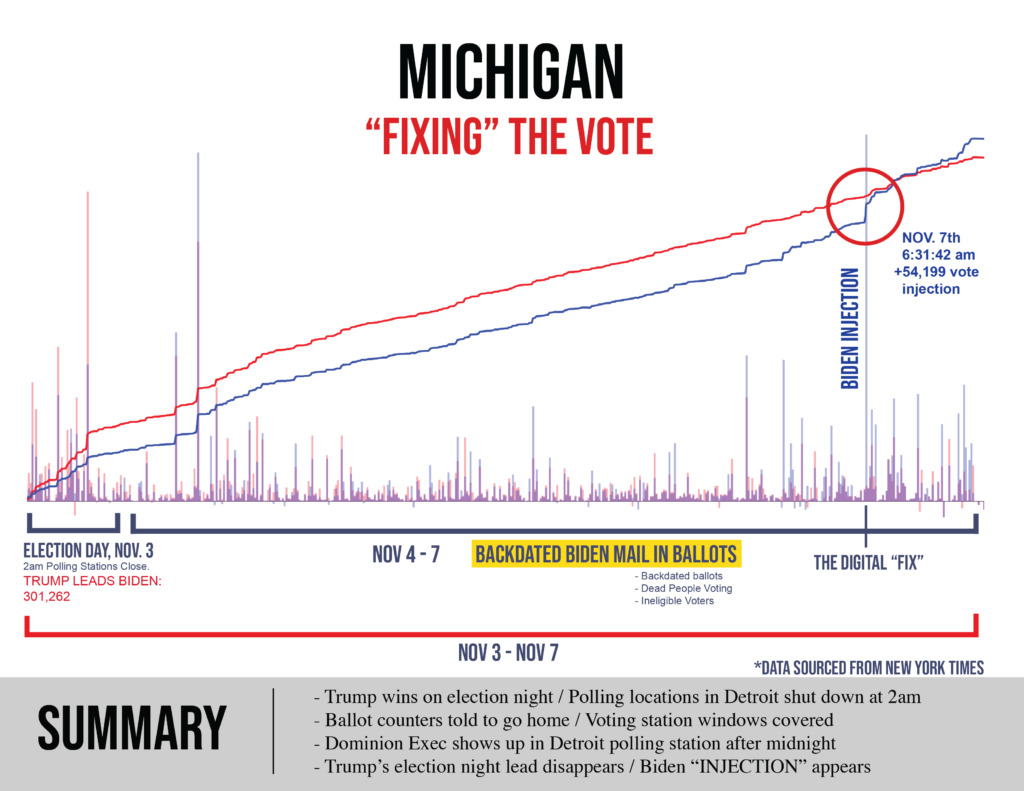
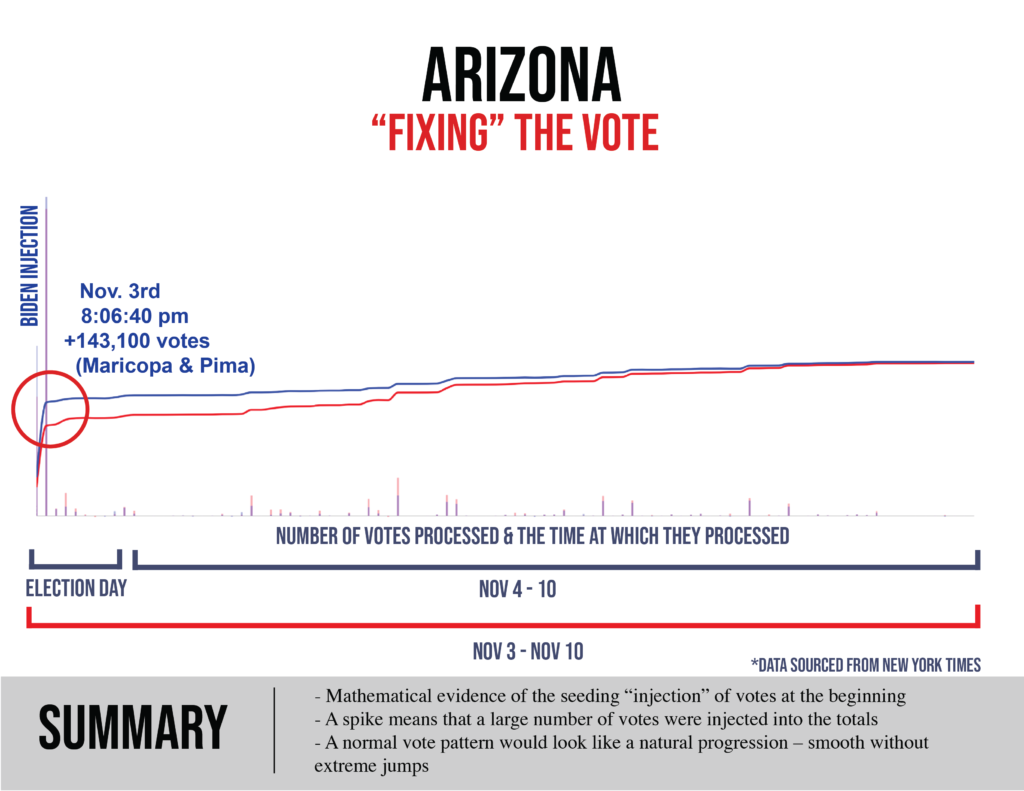
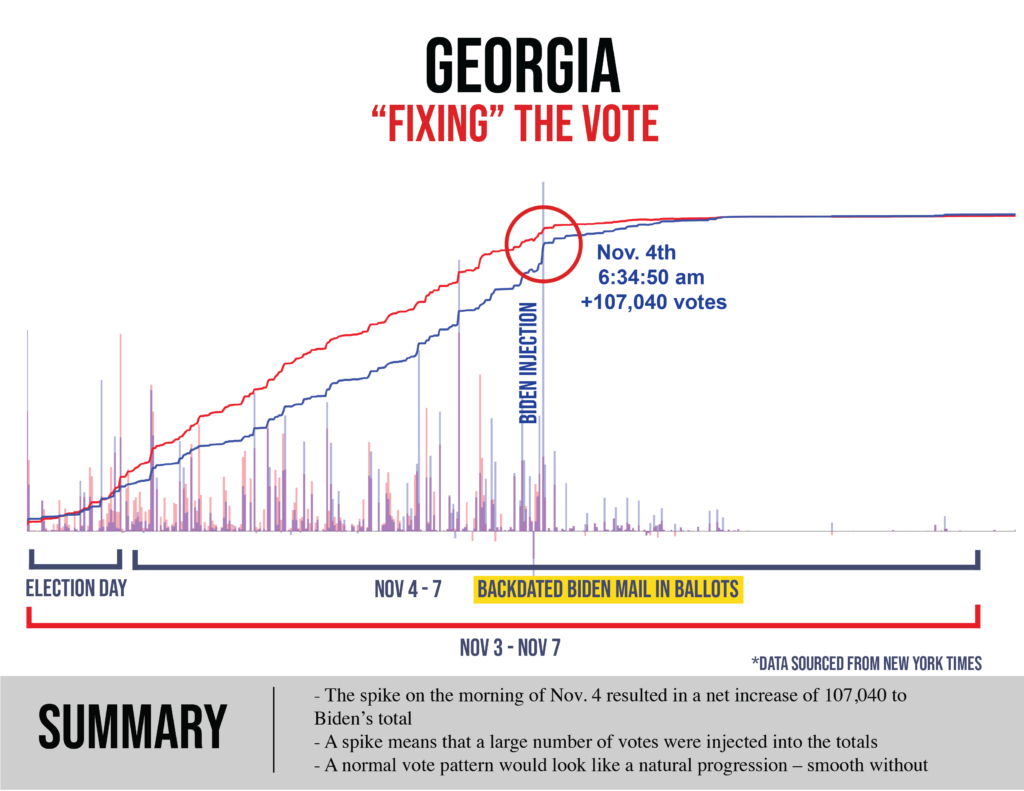
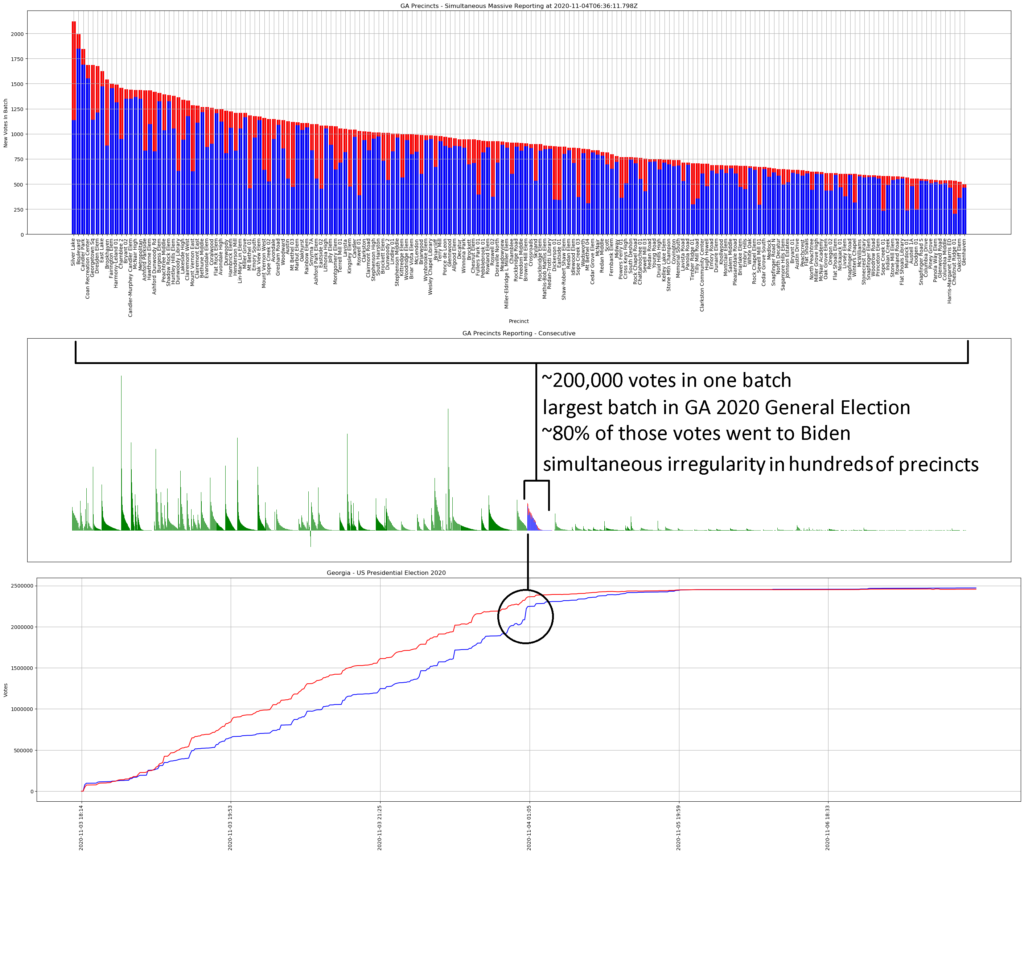
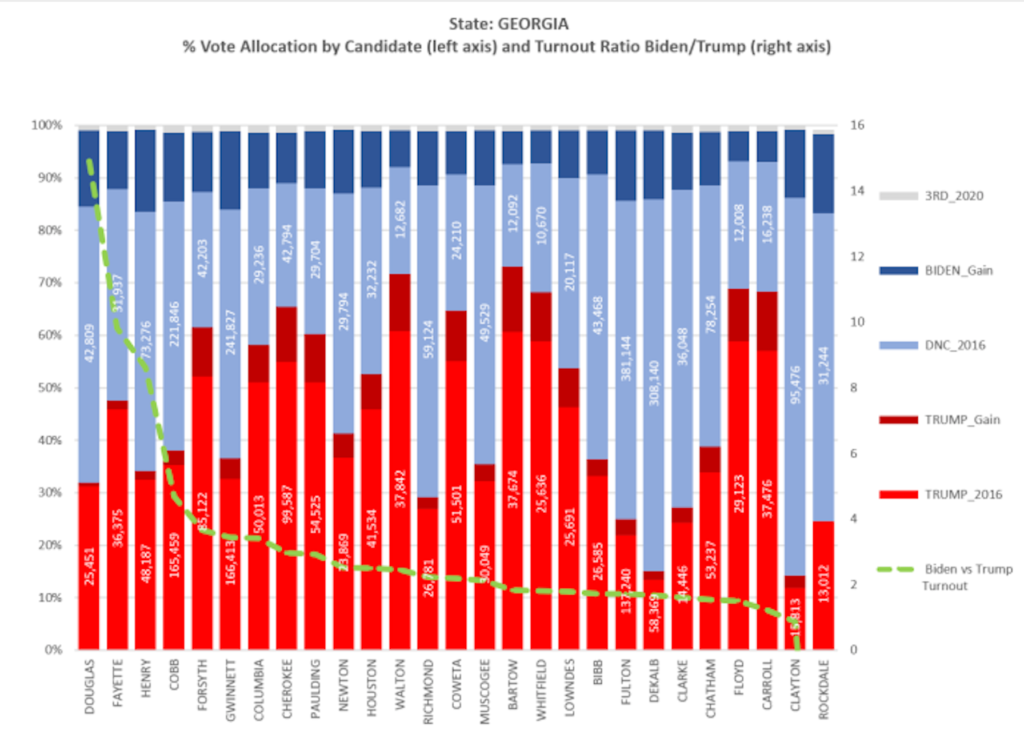
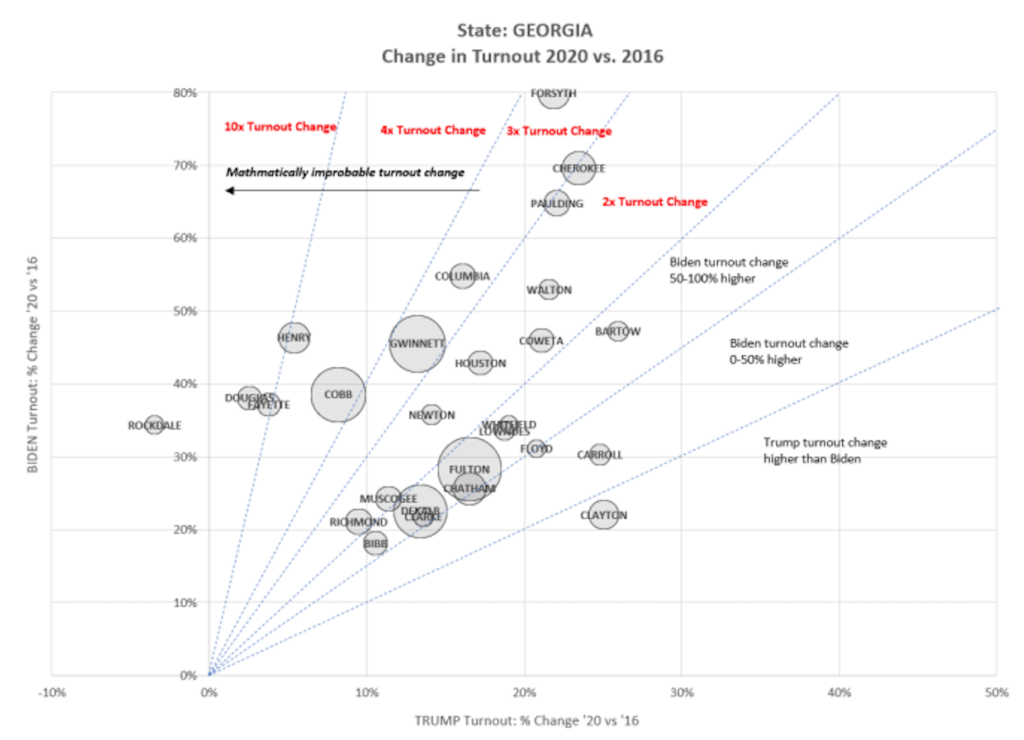
Pennsylvania official votes (@11/24 8 PM):
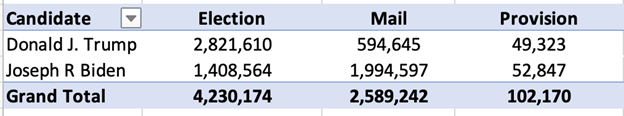
Pennsylvania reports having mailed out 1,823,148 ballots, of which 1,462,302 were returned. Yet total mail-in votes number 2,589,242? From where did the extra 2,589,242 – 1,462,302 = 1,126,940 votes come?
"Destroying the New World Order"
THANK YOU FOR SUPPORTING THE SITE!
Latest Activity
- Top News
- ·
- Everything
Catherine Fitts: Epstein, CIA Black Budget, the Control Grid, and the Banks’ Role in War
Ключові слова в тексті: як органічно їх вписати в статтю
Orwell - Football, Beer & Gambling
I, Pet Goat VI by - Seymour Studios | I, Pet Goat 6
Official Trailer NOVA '78 directed by Aaron Brookner and Rodrigo Areias
Peter Sellers - The Party (opening scene)
© 2026 Created by truth.
Powered by
![]()
You need to be a member of 12160 Social Network to add comments!
Join 12160 Social Network